My first CTF challenge writeup
Post on 31 August 2023 | 2 min read
The motive of hosting the challenge is to giveaway a Rs. 500 off coupon to the whatsapp community members by testing their CTF skills.
Let's begin solving the challenge.
Challenge category: Web
Difficulty level: Easy
Challenge link: http://munazir.com/leaf
Part 1:
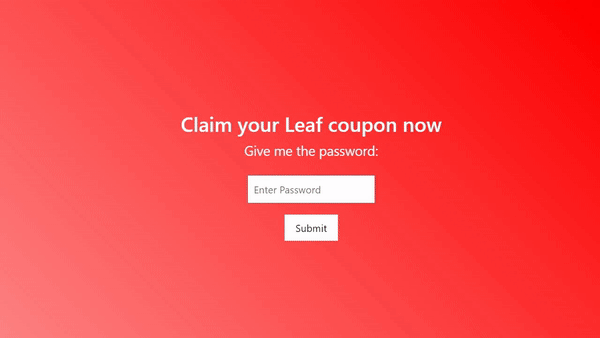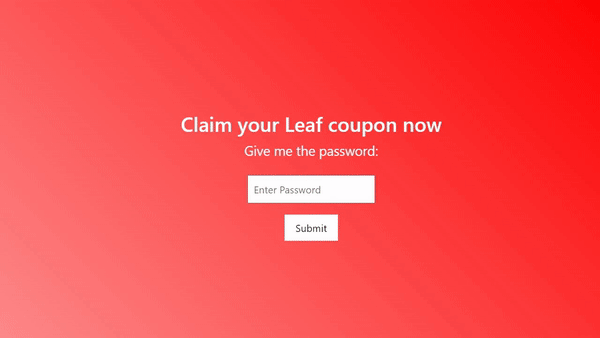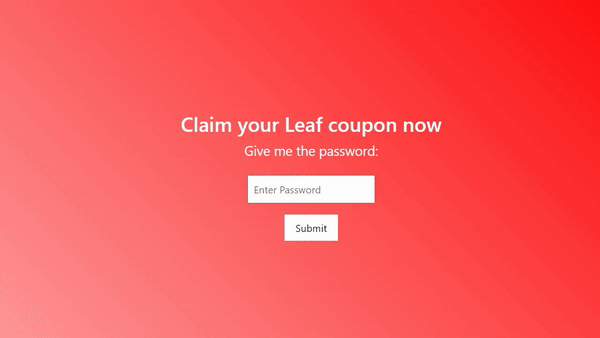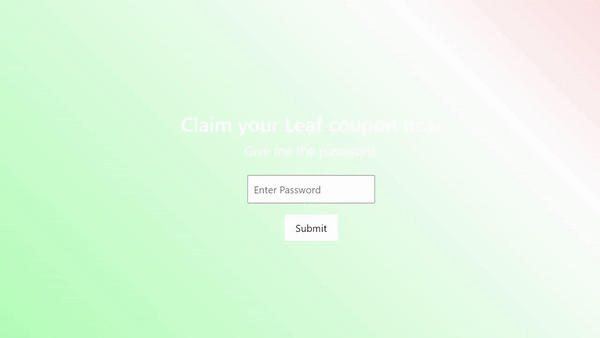
On visiting the challenge page, we can see the input field which requires password. Right click is disabled on the page to prevent users from viewing the source code. But we can easily bypass this page in multiple ways
1. Prepend 'view-source:'' in the URL.
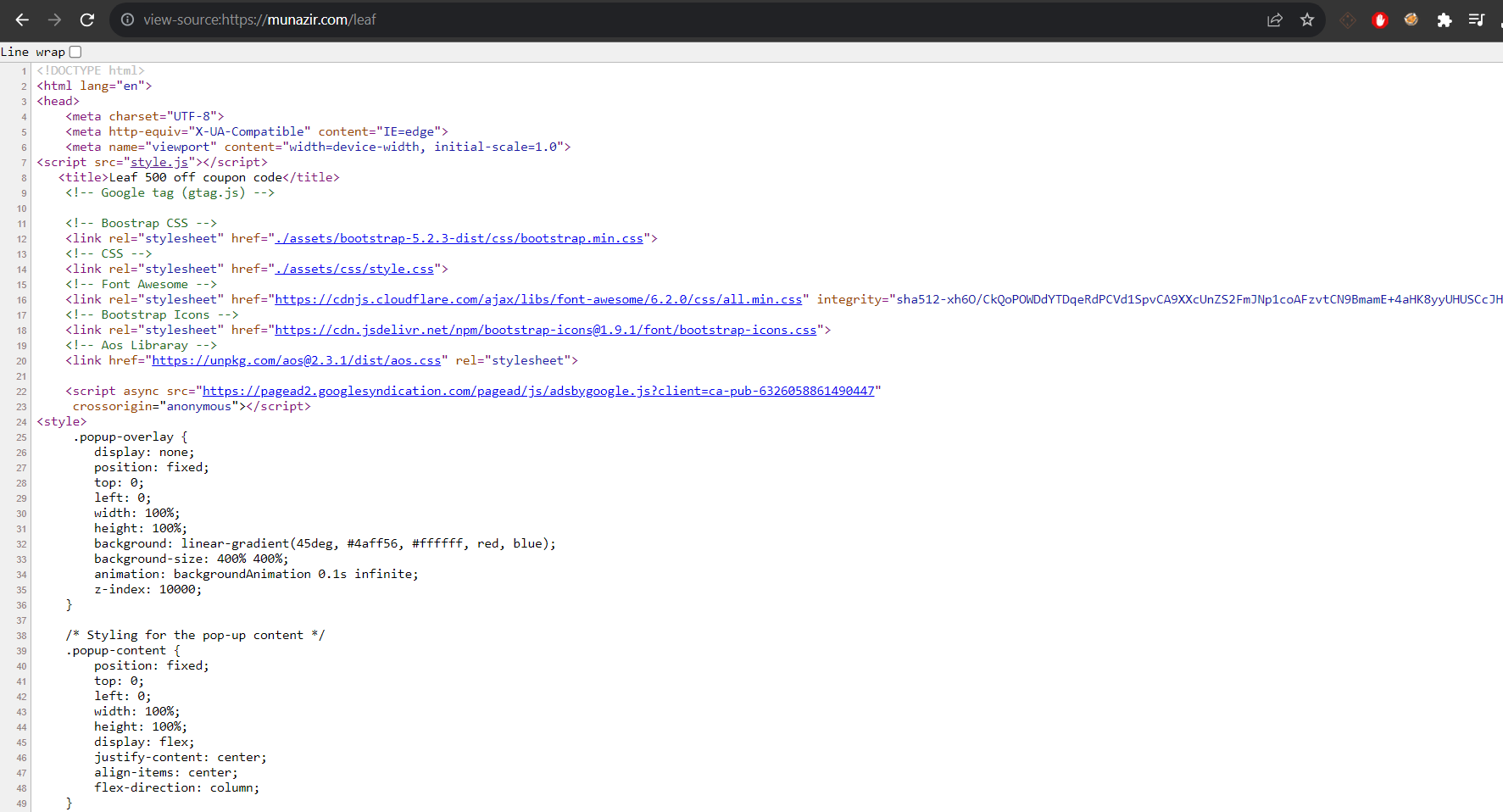
2. Using ctrl+shift+c, we can see the developer option and view the page source.
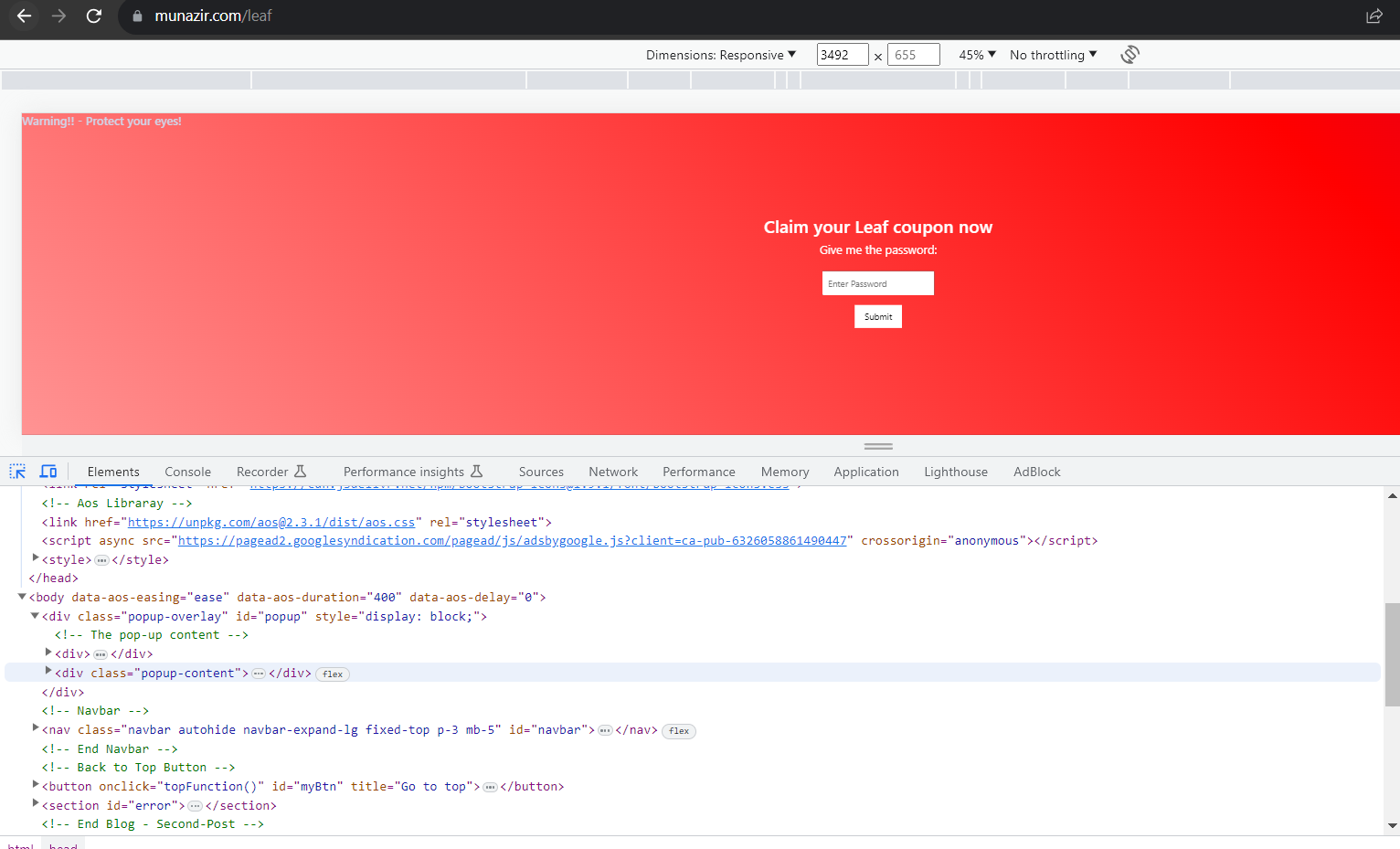
Upon viewing the page source, we can easily bypass the password page and recover the hint
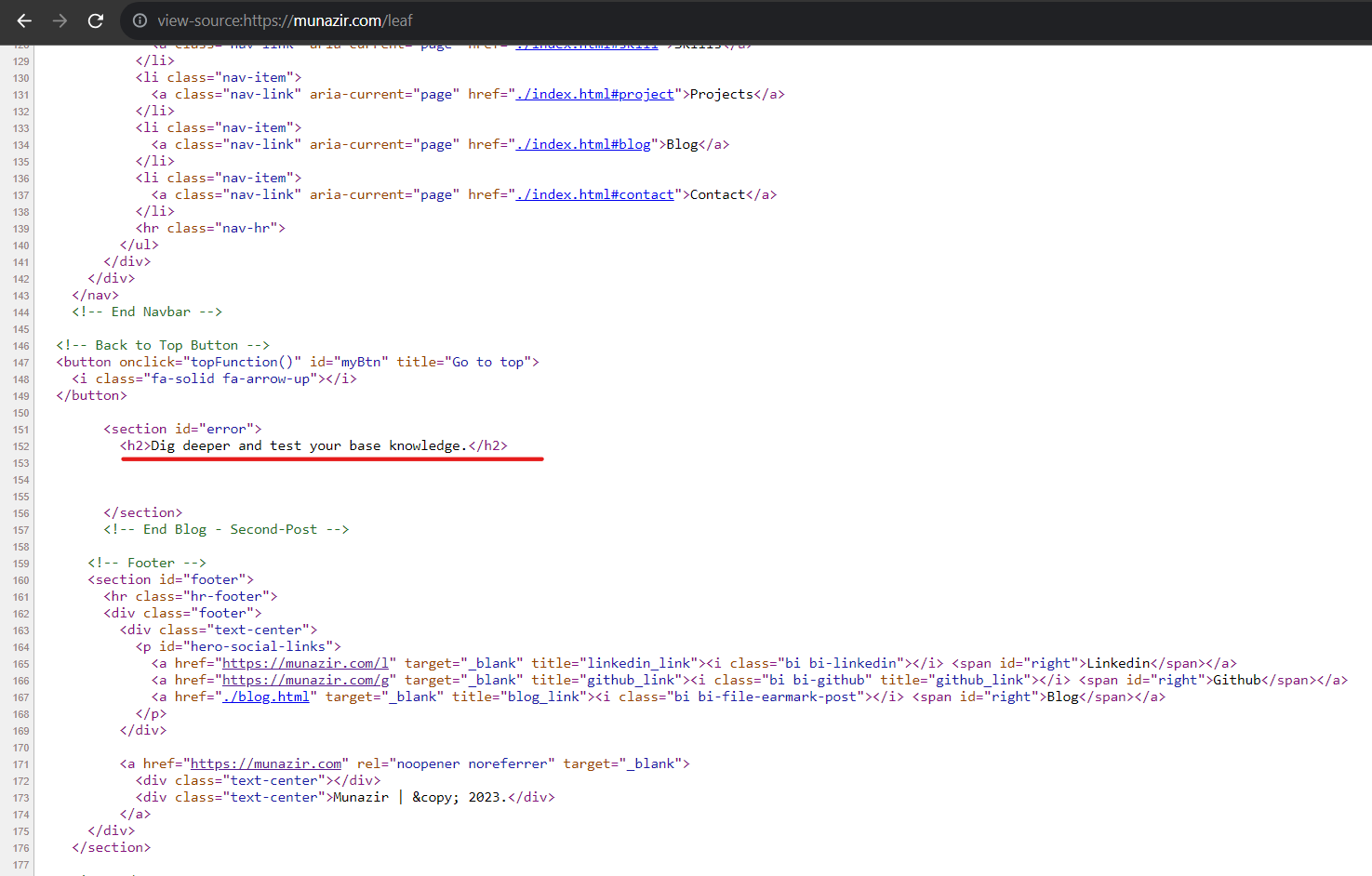
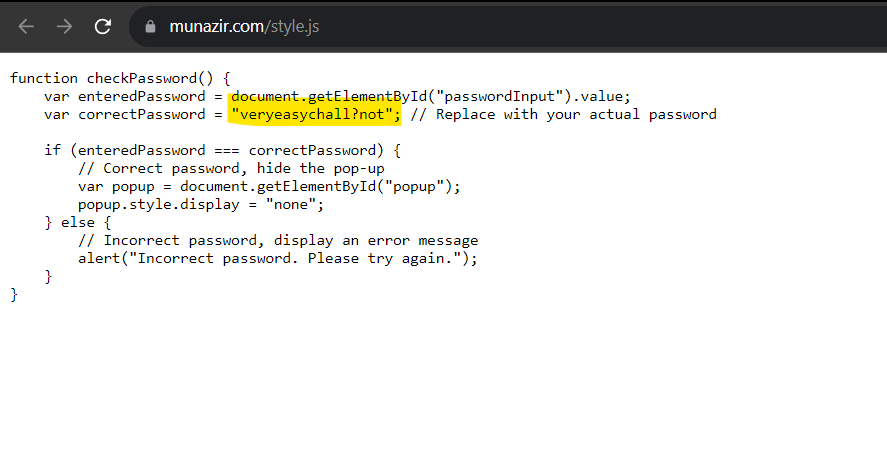
We can also retrieve the password and bypass the page using password stored in the 'style.js' file.
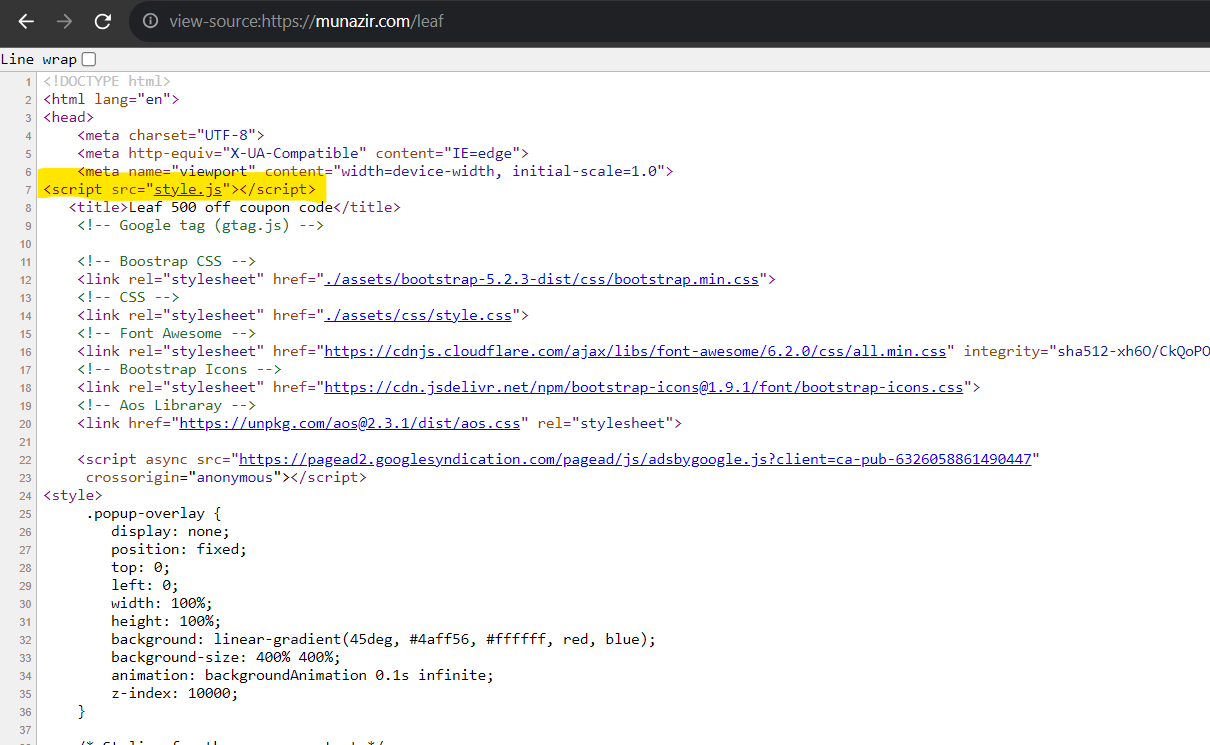
Visit style.js and copy the password.
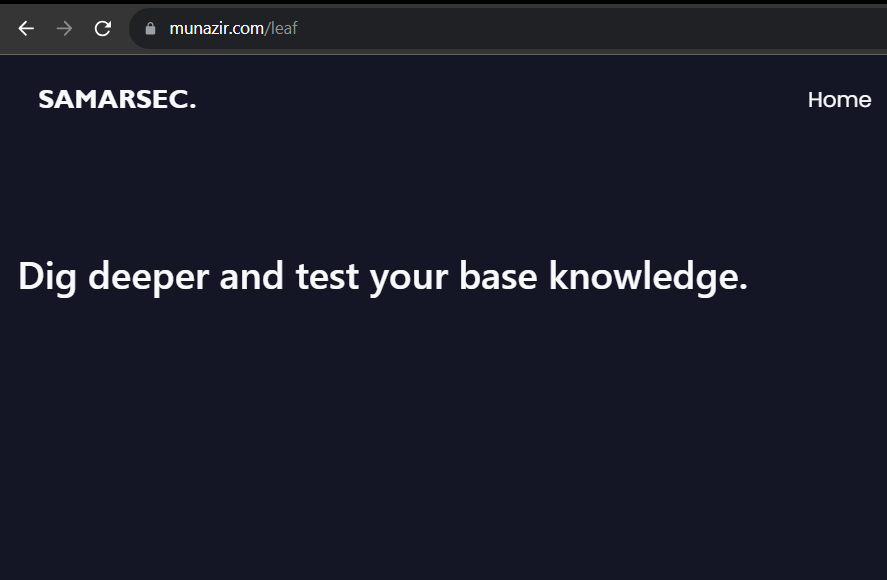
We have successfully bypassed the page:
Part 2:
Now it's a tricky and main part of this challenge.
The hint says "Dig deeper and test your base knowledge."
There are two parts in the hint: "Dig deeper" and "Test your base knowledge"
In the first part, we can observe the word 'Dig'. From this word, we can recall a tool called 'Dig' - Dig is basically a network administration command-line tool for querying the Domain Name System (DNS).
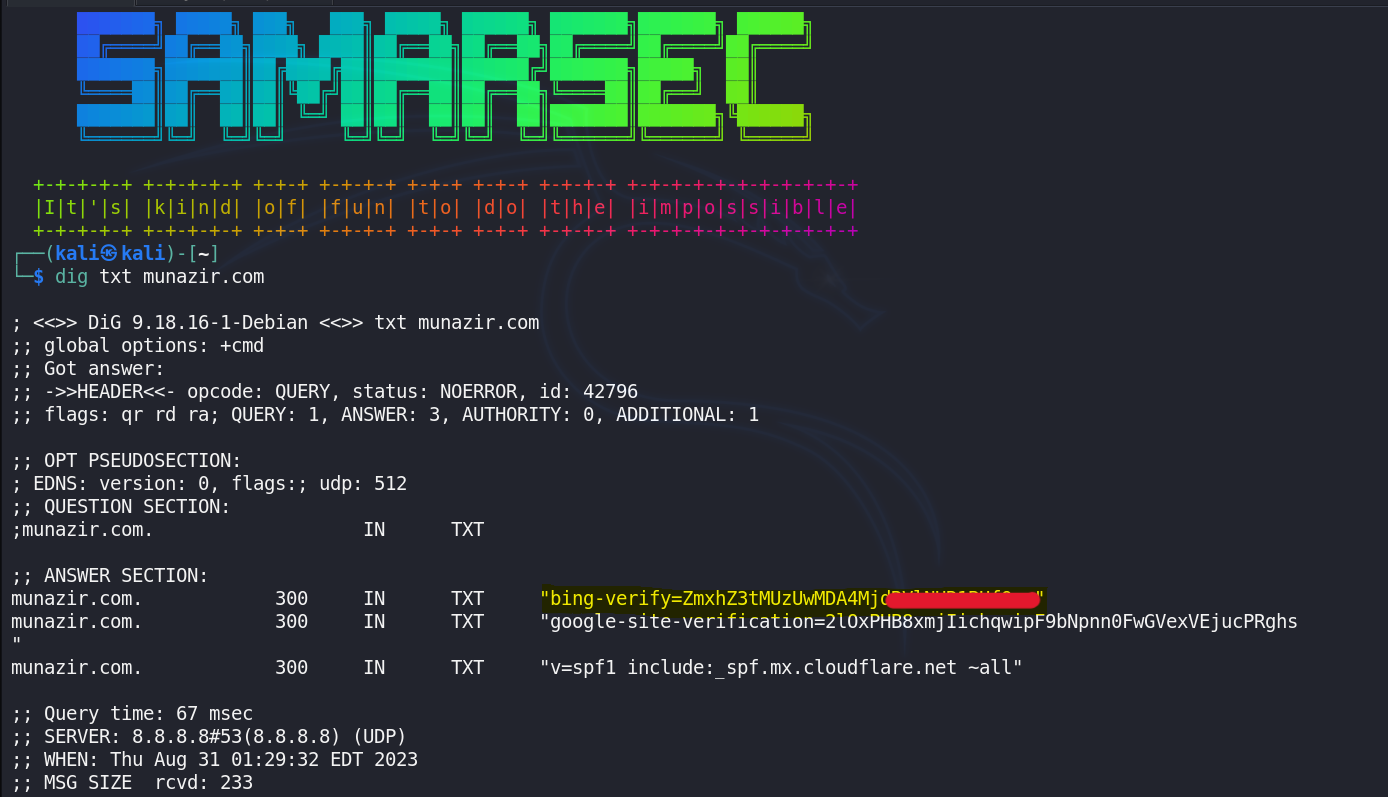
So, let's look at the DNS records of the domain, specifically TXT record: By using the command 'dig txt munazir.com'
we can observe a TXT record bing-verify="". Generally Bing does not use the same format used in the TXT record on the domain to verify the ownership.
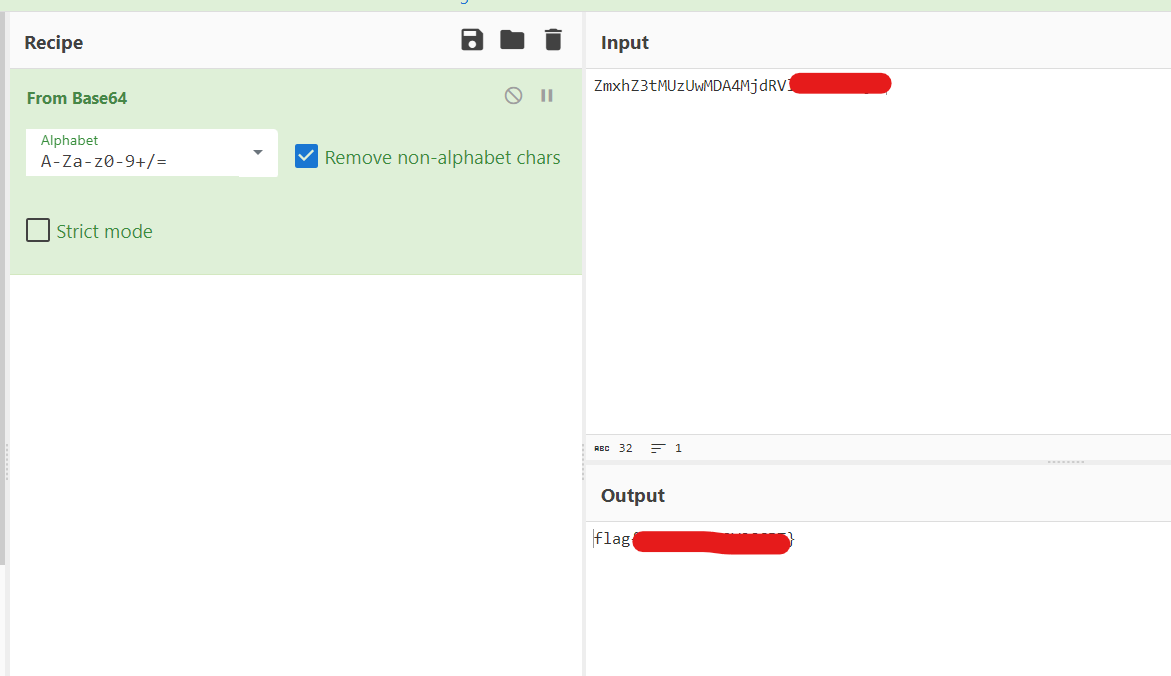
Now let's come to the second part of the hint "Test your base knowledge", The value mentioned in bing-verify is base64 encoded.
We can easily decode this base64 encoded string using CyberChef.
The flag obtained by decoding base64 string contains the Coupon code.
Wasn't the challenge easy?
Congratulations to those who managed to solve the challenge!
Stay tuned for more CTF writeups and join the whatsapp community.
Happy hacking!!
Back to Home
